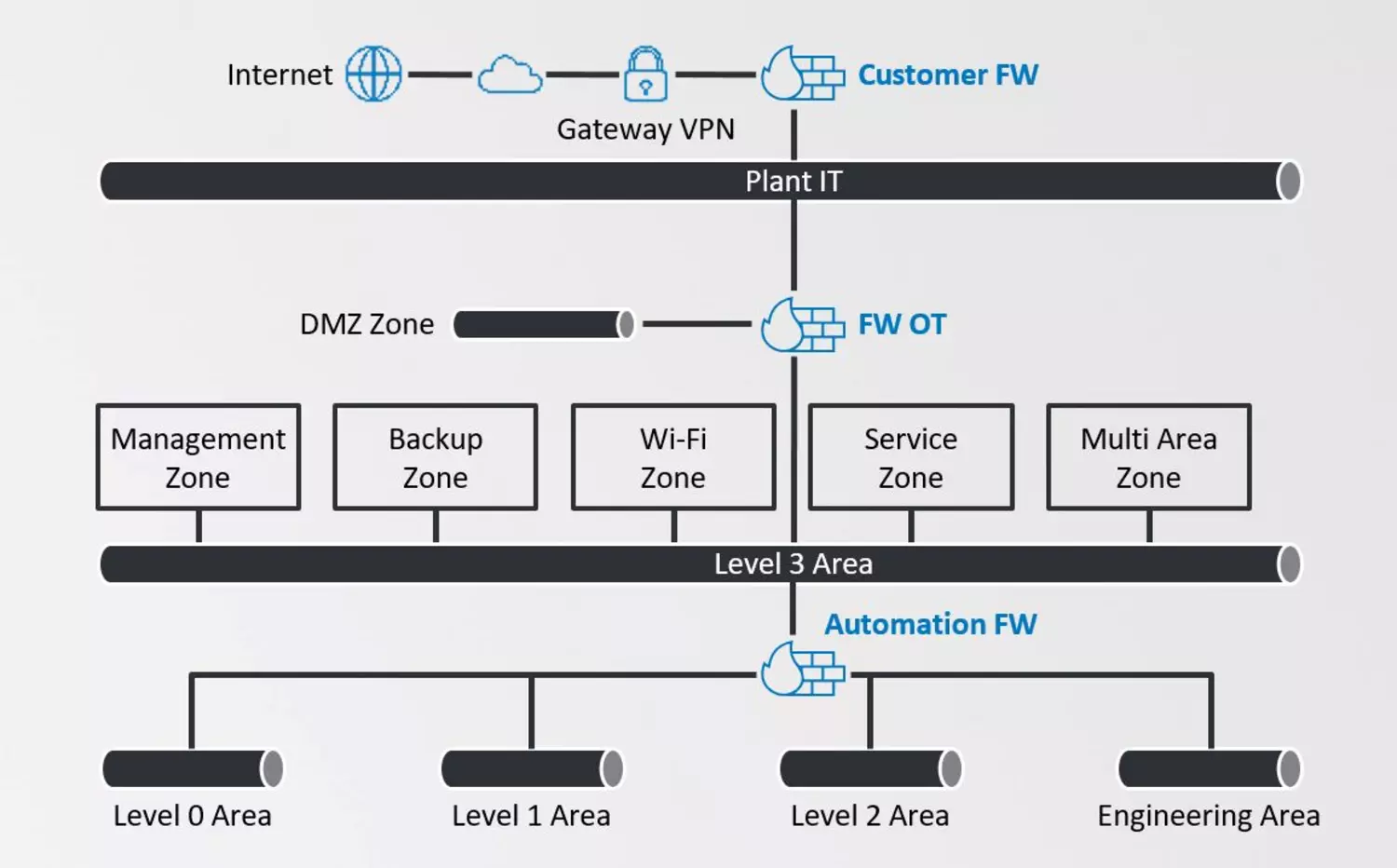
IT/OT security for the customer-specific automation infrastructure
With our Defense in Depth approach, we protect IT/OT infrastructures from cyber attacks and so help to secure high availability levels for the plants and equipment concerned. For this, we use a modular system consisting of various tools that suit the customer's individual requirements.
Customer challenges addressed
- Plant availability in a changing threat landscape
- Potentially high risk of inadvertent attacks (ransomware)
- Continuous risk management
- Application of security updates that take all relevant aspects into consideration
- Monitoring and evaluation of system events
- Disaster recovery capability
- Support throughout the lifecycle of the plant
Key features
- Avoidance of production stoppages
- Risk and related asset management
- Zoning and authorization model of the OT infrastructure and its components
- Centralized logging with optional anomaly detection
- Continuous monitoring of critical components
- Consideration of the requirements of IEC 62443
-
Risk assessment
Risk analysis as foundation for security concept
As part of a risk analysis, our experts examine your plant's infrastructure together with you; this applies equally to existing plants in operation or to new installations. The risk analysis covers the installed components and the relevant availability, integrity and confidentiality requirements, thus enabling an evaluation to be made of the risk to the overall plant. Appropriate security measures are then defined for each individual case in order to reduce the extent and probability of any potential damage identified.
![]()
Example: TARA (Thread and Risk Analysis) -
Implementation of security measures
Security tailored to your needs
This section is where the previously identified measures are put into practice, such as network zoning of components (and their groups), the associated implementation of firewalls, or the installation of monitoring and logging systems to determine the status of individual components. In the next step, individual components are protected by system hardening.
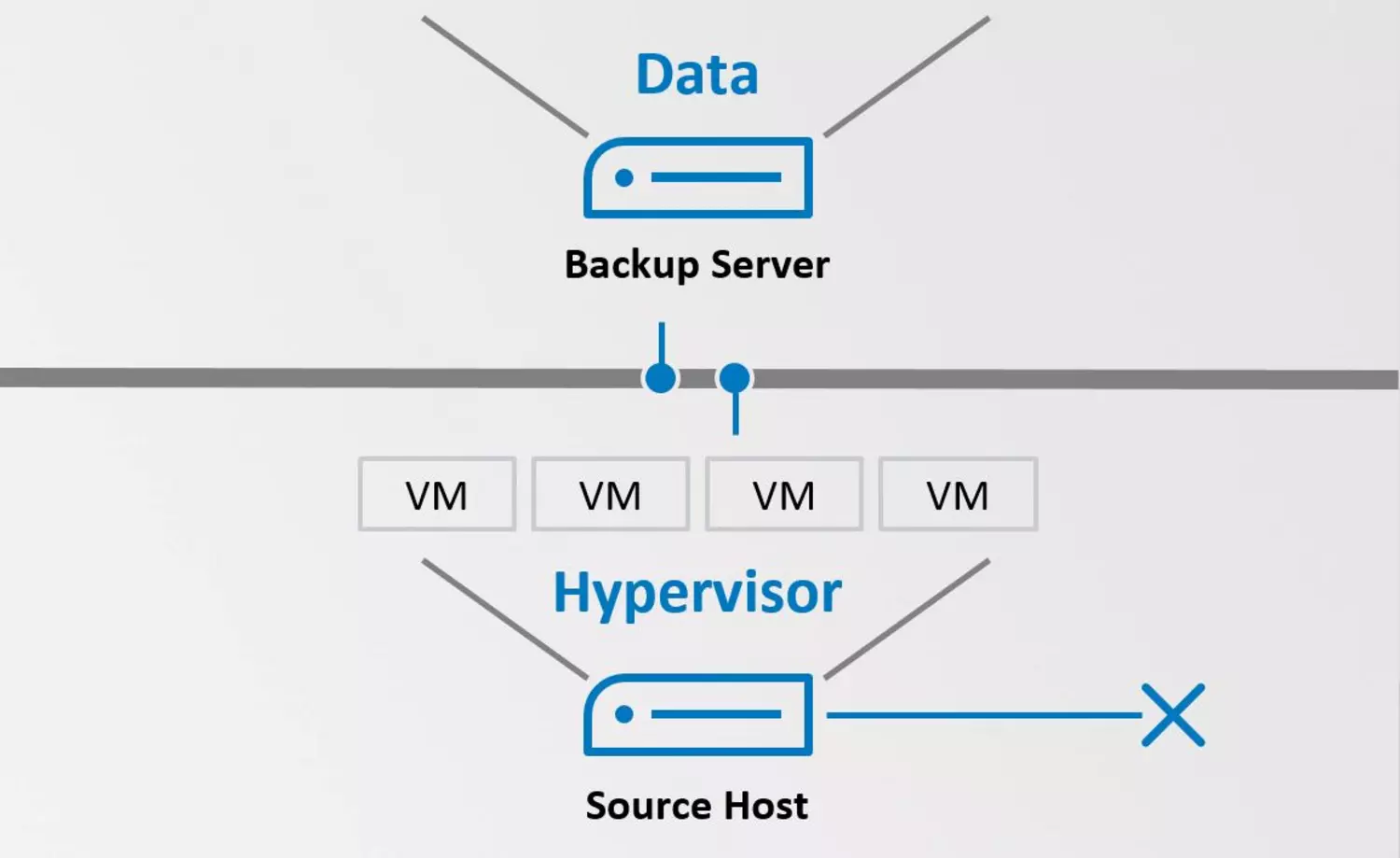
The scope could also include an endpoint security solution (antivirus protection), patch management, or data backup. The individual measures depend on the customer's requirements and may complement measures already in place.
![]()
Example: Zone & conduit concept -
Standard service
Operation of security measures
With this service package, SMS group experts ensure that the security measures implemented are fully functional. This includes support with installing updates and making any necessary configuration changes, monitoring the availability of the network infrastructure, log analysis for unusual events, as well as completing regular virus scans including reports. In addition, data backups are included in the package.
![]()
Example: Displaying the health status of the systems -
Extended service
Keeping security measures continuously up-to-date
Due to the constantly changing threat landscape, we recommended keeping security components continuously up-to-date and replacing them after a certain time in use. The extended service package is offered for this purpose.
This includes, among other things, a regular risk assessment and recurring evaluation to determine whether any measures taken are sufficient or whether additional action is required.
The package also includes asset and vulnerability management and data can even be backed up in the cloud. Not only that, regular recovery tests are included in the extended service package so that, in the worst-case scenario, the system can be restored and corrupt data can be identified and cleansed in advance.
If our experts identify new vulnerabilities in the installed components, you will be supported with workarounds if no updates are available.
![]()
Example: Vulnerability scanner & penetration test
Use our contact form for questions, inquiries or personal contact.